This is the original text of a talk I wrote for the Tallinn Digital Summit 2024, which was built around the theme of Securing the Digital Tomorrow.
Introduction
I’m going to be talking about how decentralized systems can be more resilient not only to attacks, both from the outside and in, whether these are technical or social, but also how they can withstand attempts at being co-opted.
Now, there are circles where decentralization has become a dirty word, and it’s understandable.
Throughout the last few years, it got mostly associated with crypto assets, and that space has seen some massive blow-ups.
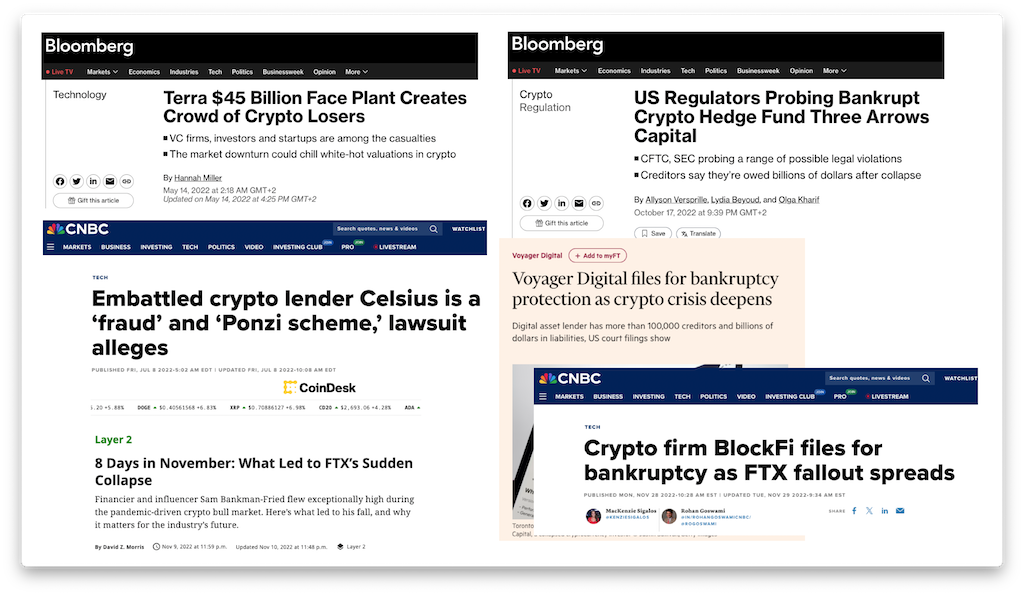
While I do not intend to spend most of my time on crypto, I want start with this garish catalogue of failures.
The Big Blowups Of 2022
This chain reaction with culminated with the FTX explosion started when Terra went down, taking Three Arrows Capital with it, a fund that became patient zero for the contagion that would last months.
Now, why did all these companies go down with it?
It wasn’t lack of regulation, because all of them were operating from jurisdictions where they were regulated.
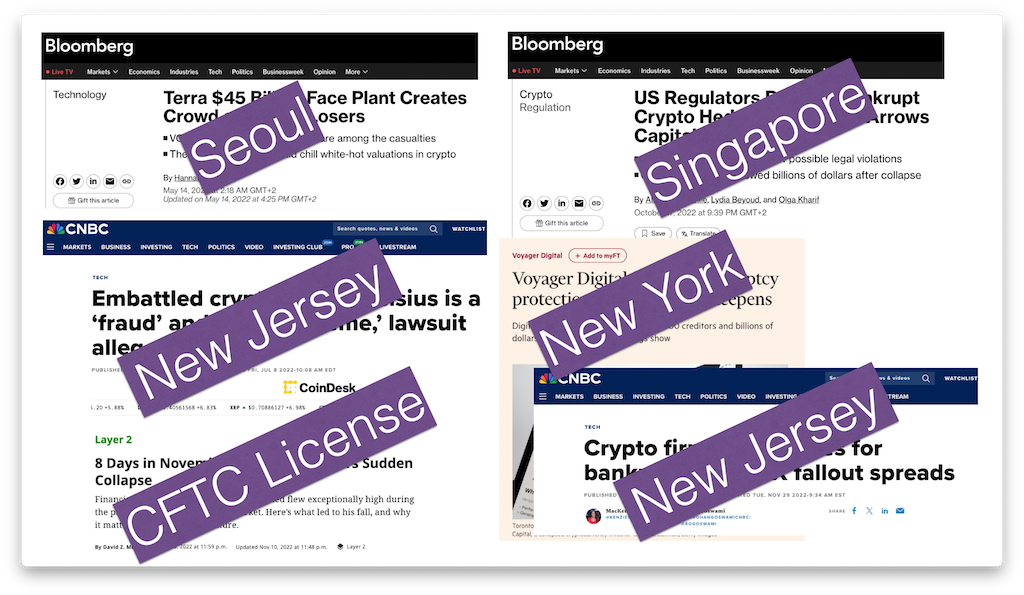
Most were in the crypto lending business, but that wasn’t what killed them.
At the same time that you had these companies blowing themselves up, other projects like AAVE and Maker, kept operating just fine - even though both were in the lending business as well.
It’s also not an issue of scale, with the smaller ones having an easier time adapting - both AAVE and Maker each had the same amount of assets under management that some of them like Celsius did ($12Bn).
What all these implosions had in common with each other was the fact that they were all centralized systems.
While in theory Terra was a decentralized project, in practice all decisions were made by a small group, and those affected the entire network. Exposure to Three Arrows Capital or FTX was such death sentence because all those who went down had issued them unsecured loans.
They had convinced the businesses that “they were good for it” and, on each case, a human made a call to lend out depositors’ assets, while said depositors believed the promises that their money was being safeguarded.
AAVE and Maker, on the other hand, were public protocols running on a decentralized network. The code governing the loans and the money flow were there for anybody to scrutinize.
When they borrowed from a smart contract - which 3AC and Alameda Research also did - there wasn’t anybody there who would believe a pinky promise of “we swear we have money”.
If you wanted to borrow, you had to overcollateralize your loan.
If it started going underwater, your collateral got liquidated.
If you wanted it back, you had to pay the loan and interest.
In fact, at the same time that 3AC and Alameda kept stating that their funds were tied up and they could not currently send money out to creditors, you could also see their on-chain actions where they were transferring money to these protocols to repay their loans so they could get back their collateral and salvage something.
Malfeasance resilience
The reason why decentralized systems kept working, while centralized lenders failed, was a simple one:
Any form of centralization is a honeypot.
In this case, the attackers targeting the honeypot were not looking to take advantage of a technical problem, but to exploit a human weakness.
And this gets us to the first way that decentralized systems help: they are more robust against organizational malfeasance, because their transparency makes it obvious if there are some shenanigans going on.
Leaving aside whatever technical resilience a decentralized, distributed platform may afford, it helped in an even more important way: the fact anyone could check what was going on provided a measure of social resilience.
And that social resilience is what I find more interesting, so let’s leave the crypto and blockchain topics aside, and talk about social networks.
Social resilience
Bluesky is a decentralized social network that doesn’t feel like one. The initial experience is that of a more traditional centralized system - think of Twitter back when it was still sane.
The architecture is gorgeous - there is no blockchain or global consensus involved, and it’s much closer to the web than anything else - but we unfortunately will not have time to go into the details (although I am happy to talk about any of these topics at length, so feel free to grab me after).
Let’s first talk about some of the social problems that Bluesky aims to address.
Problem 1: Opaque Algorithms
A huge issue that centralized platforms have comes from opaque algorithms which prioritize the content that users see by their own secret criteria.
All too often, these algorithms are geared to driving everyone towards the things more likely to create engagement, because engagement brings revenue.
This ends up leading to outrage farming and click-baity pieces as people try to maximize engagement with their content, so that it’s shown to more viewers.
Problem 2: One-size-fits-all moderation
Centralization also leads to one-size-fits-all moderation.
Moderation decisions can be well meaning: ideally you do not want people on your platform calling each other slurs, or advocating hate.
However, if a capricious owner decides that they don’t want to be called “cisgender”, and declare it to be a hateful slur, then that will automatically impose restrictions on every single user - even if it is someone stating the indisputable true fact that I am myself cisgender.
These decisions and restrictions tend to limit the number of perspectives on the network, by reducing the things people can talk about, or the discussions that get visibility, and by attempting to narrow down the content that they consume into a few easily classifiable buckets that can then be advertised to.
Avoid monocultures
What this does is that it creates monocultures, and monocultures are very fragile things, easily taken over or destroyed by a single virus.
Bluesky’s design helps address this in multiple ways.
Your default feed is a chronological view of the people you have chosen to follow.
There is a built-in algorithmic view, called Discover, but where it gets interesting is that you are not constrained or shoehorned into it.
Anyone can build their own algorithmic feed, with whatever criteria they design, and there is a whole community of people building different views of the network.
Feeds that show comments by people you follow who are usually quiet, feeds that amplify and prioritize posts by black creators, feeds that show you only pictures of mushrooms.
Bluesky also allows for composable moderation. While they do provide some baseline, common sense moderation themselves - no hate, no call to violence, no abuse - this can’t be expected to cover everything people may not want on their feed.
Say, some people may not want to see anything about cryptocurrencies, no matter if they follow the poster or not.
Or they may want to be warned if someone whose post they are seeing has a history of posting misleading content (regardless if the current post is factual or not).
Bluesky addresses this through labelers, which work for both posts and accounts.
Anybody can create a labeler, and anybody can subscribe to any public labeler.
For instance, I subscribe to a labeler that adds a tag and a content note to screenshots from Twitter, Facebook, or Truth Social.
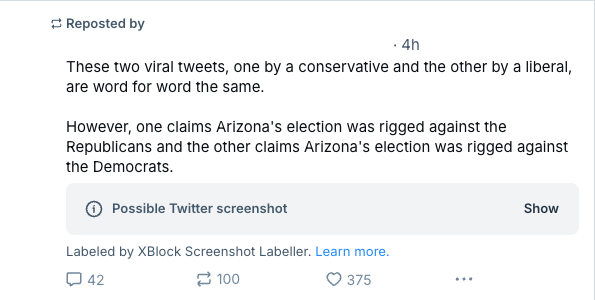
The reason why I do it is because all too often people bring these in just to dunk on others, and I may not want to be consuming this content right now. Having a label gives me a choice.
Someone else may not want to see it at all and - say - choose to hide any screenshot from a Trump post.
These are not just neat features. I think these are fundamentally important changes.
When you compose these labelers and custom feeds, what every individual ends up with is a personalized view of the network, but more importantly, it is a view of the network that they chose themselves, and that is likely to be different from the view that even other users similar to them end up choosing.
It means that as a participant on the network you are not stuck in the single context that the network imposes on you.
It also means that you aren’t lumped together with people the algorithm has determined are similar to you, or fed the same stuff to.
Not only do I think this is likely to have a positive impact on the spread of disinformation, as there isn’t one algorithm to game, but I expect that any customization someone can do to their experience is net positive.
It introduces some delta on the individual’s perspective, even while they are within a group, and will reduce the risk of monocultures.
It is the same thing we see in species: even small mutations help diversify the perspective gene pool, and can lead to a more resilient population.
Problem 3: Lock In
Now… in theory Bluesky could also turn these features off at any point when either the company turns evil, or it gets sold to someone with ill intent.
However, Bluesky is built on the Authenticated Transfer Protocol, or ATProto, which is designed to power decentralized content networks.
While the data for most users is currently hosted by the Bluesky company, it doesn’t need to be - anyone can run their own Personal Data Storage, if they choose to, which integrates transparently into the network as it exists.
They do not need to ask for Bluesky’s permission to do it.
You also don’t need to apply for verification: you can bring in your own identity as a domain you control - something that the Bluesky company can never take from under you.
And the reason why all this is possible, and why you can rely on that continuing to work even if Bluesky the company were to turn evil, is because Bluesky the application is nothing but a open source view on the data available on the network.
This network can choose to transition and keep operating without them.
Given anyone can provide the exact same service to users, through their own application, without any loss of content or social graph, then Bluesky is disincentivized from acting benevolent as it grows, but then turning against its users once they have hooked them.
ATProto is designed so that a billionaire could spend the GDP of Estonia acquiring the platform, and they still would not gain control over the network - they would only acquire a single access point.
And this is because ATProto does not trust Bluesky.
Co-option resilience
This is fundamentally important, because any large enough network will eventually be an attractive target to co-opt - the potential to drive the perspective of dozens or hundreds of millions is just too appealing.
Therefore, you cannot depend on promises of benevolence, or on having the “right person” in charge - user control needs to be built into the protocol.
This second case of resilience is even more important for me: decentralized systems can provide a measure of durability against being captured and subverted against their users.
Now, this architecture has other advantages for Bluesky, including that it provides a clear path to offering services to users, but it also removes some potentially thorny problems for them.
Namely: data can be a liability.
Data is a liability
Because to elaborate on a line from Jim Balsillie, “Data is not the new oil, it’s the new plutonium”.
Again, keep in mind that centralization is a honeypot. The larger your system, the more data you keep, then the more appealing it is going to be for attackers.
And the problem with playing defense is that as a defender you need to succeed every time, whereas attackers only need to succeed once.
If instead of keeping a massive data store of all your users, you let each of them keep their own data and control who to share it with and when, you are making your system much harder to attack.
In that architecture, an attacker wanting to get at your users’ data would need to hack a myriad of independent devices, where they are no longer only attempting to breach a single company’s security, but that of multiple operating system providers.
This isn’t theoretical. Just to name an example, there’s this US company called Bindle (which, full disclosure, I advised since its foundation in 2020 until its acquisition this year by iDen2).
During those four years, Bindle built the largest self-sovereign identity network in the United States, connecting over 300 issuers and 400 verifiers, and managing a range of personal information from COVID vaccination certificates to user identity verification.
They did not get penetrated once. Their system leaked no data, even though they had these hundreds and hundreds of interacting companies involved, which is a primo situation for credential leak.
I invite you to make a search of general data breaches during that period for comparison.
These are social systems
Ultimately, we are talking not just about networks, but about social systems that will be affected by there being human beings in the middle.
All these architectural decisions, the added visibility, the fact that you involve multiple parties that are empowered to act as checks and balances against each other, that users have a credible option to exit any of these systems because they retain control of their information and money, all help reduce trust.
The more decentralized a system is, the less trust you need to place on any individual party. And while it is unlikely that we will get to full trustlessness on any complex system - human or technological - we can make them more robust by reducing how much we rely on it through transparent decentralization.